Intelligence to action in hours, not months.
From processing 500,000+ real estate listings with sub-second search times to defending critical infrastructure during nation-state cyber attacks. From $65B annual transaction processing to combat logistics in Iraq. UDX delivers enterprise-scale technology that works when it matters most.
UDX brings military precision to federal technology. Founded by USMC 2nd Reconnaissance Battalion veterans, we understand that mission failure isn't an option. From securing communications in Iraq to defending democracy in Ukraine, we deliver when it matters most.

Ukraine Ministry of Digital
Technical advisor defending digital democracy during active conflict since 2022
Proven Performance
Ukraine Digital Ministry
Strategic technology advisor. Maintained critical infrastructure through invasion, cyber attacks, and power grid failures. Democracy defense in action.
USMC Logistics Command
Web-based ERP for 40-person unit. Detained combatant tracking for Operation Iraqi Freedom. Built on WordPress for rapid deployment and maintenance.
Defense Contractor Systems
SBIR/STTR solicitation platform. Asset management for $240M+ inventory. Real-time BI dashboards for government reporting.
Enterprise Scale Proven
Transact Campus acquisition. 12M users, 1,800 institutions, $65B processed annually. Enterprise reliability at federal scale.
14+
Years Zero Breaches
$240M+
Assets Managed
99.999%
Uptime Under Attack
6hr
Deployment vs 6mo Industry
UDX Corporation Capability Statement
Federal Technology Solutions | CAGE: 9V1F2
Company Overview
Socioeconomic Status
- ✓ Veteran-Owned Small Business (VOSB)
- ✓ Service-Disabled Veteran (Pending)
- ✓ Small Business
Leadership:
Founded by USMC 2nd Reconnaissance Battalion veterans with Top Secret clearance eligibility
Core Competencies
Cloud & Infrastructure
- • FedRAMP-compliant architectures
- • AWS GovCloud migration
- • Azure Government deployment
- • Zero-downtime migrations
- • Infrastructure as Code (IaC)
DevSecOps & Automation
- • CI/CD pipeline development
- • Automated security scanning
- • Compliance as Code
- • Container orchestration
- • GitOps implementation
Cybersecurity
- • Zero-trust architecture
- • NIST 800-53 controls
- • Continuous monitoring
- • Incident response
- • Security assessments
Unique Capability: "Intelligence to Action in Hours, Not Months" - Rapid deployment of secure, compliant solutions with 6-hour turnaround vs. industry standard 6 months. View all solutions →
NAICS Codes
Primary NAICS
- 541511 - Custom Computer Programming Services
- 541512 - Computer Systems Design Services
- 541519 - Other Computer Related Services
- 541611 - Administrative Management and General Management Consulting
Secondary NAICS
- 518210 - Data Processing, Hosting, and Related Services
- 541690 - Other Scientific and Technical Consulting Services
- 541990 - All Other Professional, Scientific, and Technical Services
- 561210 - Facilities Support Services
Past Performance
| Client | Project | Value | Period | Status |
|---|---|---|---|---|
| Ukraine Ministry of Digital Transformation | Strategic Technology Advisory - Critical Infrastructure Defense | Classified | 2022-Present | Active |
| US Marine Corps Logistics Command | Web-Based ERP System (40-person unit) | Multiple Contracts | 2012-2018 | Complete |
| USMC Special Operations | Detained Combatant Tracking System (OIF) | Classified | 2003-2008 | Complete |
| Lockheed Martin | SBIR/STTR Solicitation Platform | $500K-$2M | 2017-2018 | Complete |
| Defense Contractor (Unnamed) | Asset Management System | $240M+ Managed | 2015-2020 | Complete |
| Transact Campus (Commercial) | Enterprise Payment Platform | $1.6B Exit | 2008-2019 | Acquired |
| Red Door Company | Real Estate Intelligence Platform - Case Study | 500K+ Listings | 2020-Present | Active |
| Disco Donnie Presents | Festival & Event Management Platform - Portfolio | 15K+ Deployments | 2016-Present | Active |
Additional case studies and references available at udx.io/work
Key Differentiators
Why UDX
-
Combat-Tested Leadership
USMC 2nd Recon veterans understand mission-critical means life or death
-
Rapid Response
6-hour deployment capability vs. 6-month industry standard
-
Zero Breaches Since 2011
14+ years protecting critical infrastructure
-
Enterprise Scale Proven
Proven Scale
$1.6B
Enterprise acquisition value delivered
12M+
Users on platforms we've built
99.999%
Uptime under cyber attack
Contract Vehicles & Certifications
Current Vehicles
- • Direct Award Capable
- • Subcontractor Ready
- • GSA MAS (In Process)
- • CIO-SP4 (Planned)
Contract Types
- • Firm Fixed Price (FFP)
- • Time & Materials (T&M)
- • Cost Plus Fixed Fee (CPFF)
- • IDIQ/BPA Capable
Certifications
- • ISO 27001 (In Process)
- • SOC 2 Type II (Planned)
- • FedRAMP Ready
- • CMMC Level 3 (Target 2025)
Contact Information
Business Development
- Via Contact Form
- udx.io/contact
- Federal Portal
Corporate Headquarters
- Durham, North Carolina
- Research Triangle Region
- udx.io
Additional Resources
Security-First Architecture
Defense-grade security frameworks proven in combat zones and under nation-state cyber attacks. Every system we build starts with zero-trust principles and continuous compliance.
Zero-Trust Security Model

Secure Authenticated Access Architecture
Multi-layer authentication and authorization framework with continuous verification. No implicit trust, even for internal systems. Every request is authenticated, authorized, and encrypted.
Certified Security Pipeline

Continuous Security Validation
Every code commit scanned. Every deployment validated. Every vulnerability tracked. Automated compliance checks ensure FISMA, FedRAMP, and NIST requirements are met before production.

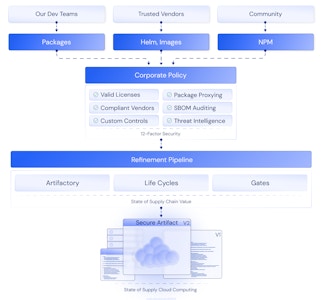
Supply Chain Security
End-to-end supply chain integrity verification. SBOM generation, dependency scanning, and artifact signing ensure no compromised code enters production systems.
Secrets & Key Management
Hardware Security Module (HSM) Integration
FIPS 140-2 Level 3 validated key management. All cryptographic operations performed in hardware-protected environments. Secrets never exist in plaintext, even in memory.

Ephemeral Security Environments
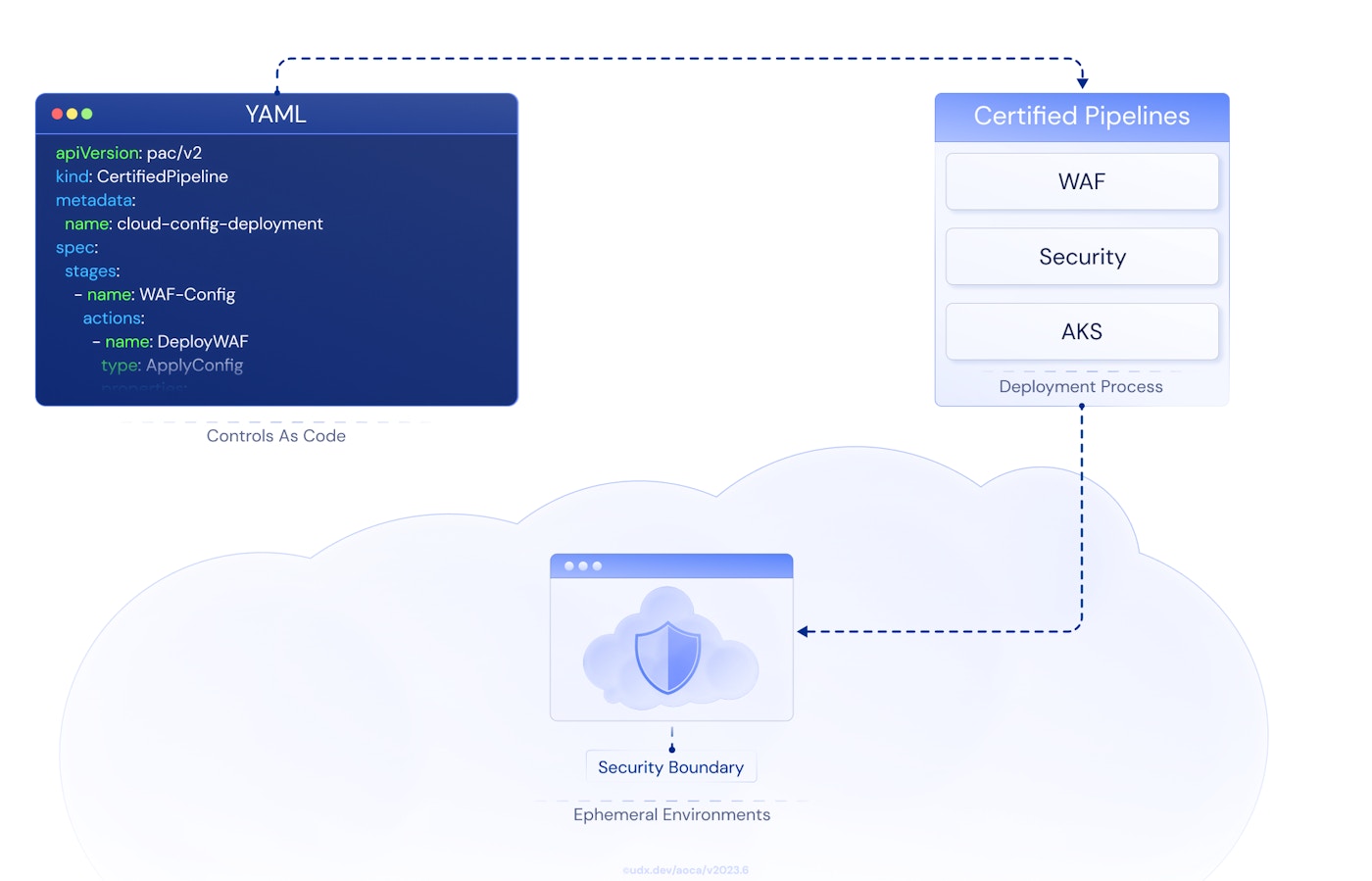
Isolated Testing
Every deployment gets its own isolated environment. No shared resources. Complete network segmentation prevents lateral movement.
Auto-Destruction
Environments automatically destroyed after use. No persistent attack surface. All data wiped using DoD 5220.22-M standards.
Compliance Validation
Each environment validated against security baseline before activation. Continuous compliance monitoring throughout lifecycle.
Security Performance Metrics
Security Breaches Since 2011
Incident Detection Time
Security Controls Implemented
Uptime Under Attack
Compliance & Certifications
Federal Standards
- • FISMA Compliant
- • FedRAMP Ready
- • NIST 800-53 Rev 5
- • NIST CSF Aligned
DoD Requirements
- • CMMC Level 3 (Target)
- • DISA STIG Compliant
- • DoD IL4 Ready
- • CUI Handling Capable
Industry Standards
- • ISO 27001 (In Process)
- • SOC 2 Type II (Planned)
- • PCI DSS Compliant
- • HIPAA Compliant
Cloud Security
- • AWS GovCloud Ready
- • Azure Government
- • CSA STAR Aligned
- • CIS Benchmarks
Production-Proven Security at Scale
Our security frameworks protect everything from 500,000+ real estate listings to $65B in annual transactions. Every system built with defense-grade security from day one.
Real-time threat monitoring across all client deployments. Learn about our government security initiatives →
Ready for Defense-Grade Security?
Whether you're defending against nation-states or securing citizen data, we bring battle-tested security to your mission.
What we actually do
We're not consultants who hand you a PowerPoint and disappear. We're engineers who build, deploy, and maintain the systems that keep government running. Here's what that means in practice:
Move to the cloud (securely)
We migrate legacy systems to AWS GovCloud, Azure Government, or wherever you need. Everything stays FedRAMP compliant. No downtime. No data loss. We've done it hundreds of times.
Automate your deployments
Stop waiting weeks for releases. We build CI/CD pipelines that scan for vulnerabilities, check compliance, and deploy automatically. Your developers ship faster. Security sleeps better.
Lock down your systems
Zero-trust architecture. Continuous monitoring. Incident response in minutes, not hours. We implement NIST controls so you can pass your audits and focus on your mission.
Connect old systems to new
That 20-year-old database isn't going anywhere. We build APIs and middleware that let legacy systems talk to modern applications. No rip-and-replace disasters.
Turn data into decisions
Real-time dashboards that actually help. We've built intelligence platforms for combat operations and budget tracking for peacetime. Same principle: right data, right time, right format.
Fix it when it breaks
Systems fail at 2 AM on holidays. We answer the phone. Our teams have security clearances and know your systems. 24/7 operations proven at scale.
How we work with government
The bureaucracy part (we handle it)
- CAGE Code 9V1F2 - We're in the system
- Veteran-owned - Qualifies for set-asides
- Cleared personnel - No waiting for investigations
- Prime or sub - We work both ways
What you can expect
- Technical briefing that skips the sales pitch
- Fixed-price or T&M - your choice
- Weekly updates, no surprises
- Documentation that auditors actually like
The proof is in the work
From real estate intelligence platforms processing 500K+ listings to enterprise payment systems handling $65B annually. Here's what we deliver:
0.2s Response Times
99.999% Uptime
6-Hour Deployment
Get Started
Start a Conversation
Headquarters
Durham, North Carolina
Research Triangle Region
Veteran-Owned Business
Ready to discuss your requirements?
Let's explore how UDX can support your federal technology mission.